How to avoid getting scammed in crypto
The most common scams & fraudulent behaviour found in crypto and what you can do to avoid them.

Crypto is a paradigm shift. It allows disenfranchised individuals to send and receive payments from anywhere; however its technological innovations allow for a broader range of applications than just payments.
Blockchain technology can in theory, represent anything that can be digitised. Title registration services, proof of ownership and freedom of speech are other features that blockchain can bring to society.
Consider the anonymous whistleblower who reports atrocities in a certain country. Governments can censor social media, but not the blockchain ecosystem. For example, a whistleblower with a small amount of ether in their crypto wallet, can send a transaction containing metadata with proof. The report is thus immortalised in the internet.
Like everything in life, with good comes bad and unfortunately, the space also has suffered from scams on a regular basis. From fake websites, to ponzi schemes and celebrity endorsements, there are several things to watch out for.
Social engineering scams
Social engineering is a form of psychological manipulation of people coaxing them into giving away confidential information.
You may have seen messages like this on social media and in emails:
If you’re having issues on your meta mask wallet kindly go to this metamask link for assistance: [...]
Suppose someone is having an issue with a certain project or company and they go to that project’s discord. They post a question asking for help and soon enough receive a DM from a stranger offering to help.
This stranger may have a helpful username, such as “Helpdesk#4444” or “Support#1234”. Sometimes they pose as an admin or moderator of that discord server with a matching profile picture.
Or perhaps you’re watching a YouTube video and the comments section has users offering help, giving advice or recommending specific traders. Quite often they even have the same profile picture of the creator.
Other times whole Discord servers and Twitter accounts are hacked, compromising the security of all users in that server or following that account.

How to avoid social engineering scams
The examples above are not exhaustive. There are elaborate social engineering scams where even smart people can be deceived.
In 2022, a crypto project lost millions of dollars because one of their developers was manipulated into giving away sensitive information.
The victim, a web developer, was approached in Discord with a request for a partnership. Through a long and seemingly innocent conversation, the attacker convinced the victim to install a javascript bookmarklet.
The reason was that their (the scammer’s) website wasn’t online yet, but that the developer (the victim) should bookmark it on their browser now and check back next week. It was a convoluted scam resulting in a significant amount of money being stolen from the project. See this for more information regarding this type of attack.
Below are some steps you can take to protect yourself from social engineering scams.
Keep your information private. If approached to request, offer help, or befriend you, do not provide personally identifiable information such as maiden name, address, date of birth or social security number. These are confidential pieces of information that can be used for identity theft.
Your keys, your wallet. Scammers may pose as tech support, a random samaritan or person with the same profile picture as someone with authority. Their approach is via direct message on social media platforms, persuading you to inadvertently reveal sensitive information or go to a website to steal assets from your crypto wallet. Do not give away any information to random untrusted individuals and NEVER click on links to websites.
It can happen offline. The scammer may pretend to work in your company or know a colleague. They may email, call or even show up in person with the intent of accessing a piece of information or a physical location. Never give away information that can compromise you or your company.
Clickbaiting ads. These may be links for fake job applications, business opportunities or appear to be giving valuable advice. The purpose of the ad is to send users to a landing page infecting them with malware or to capture their personal information. Do not download apps or provide information to websites you don’t trust.
Token scams
Crypto-tokens, often called just tokens, surged in 2017 on the Ethereum network. The Eth blockchain made it convenient to issue or sell the token, in an event called Initial Coin Offering, ICO, before the related application or service was created.
Many of the platforms and services proposed in the ICO boom of 2017 and 2018 were not created at all, with many still in development, gained little traction, or were abandoned. Several of these projects were quick cash grabs and users were left ones holding a worthless bag.

Do your own research
Do your own research (DYOR) when thinking about whether to invest in a project. Do not take other people's word for granted because you don't know their true motives.
It is worth remembering many influencers are paid to promote products, and the same happens with cryptocurrencies. They push their followers to buy into the XYZ token, and have been seen in a number of cases, use their followers as exit liquidity.
Here are some points to help you with your research:
- What's their unique selling point? Perhaps other projects doing the same thing. Why is this one better?
- How are the tokens distributed? Where does the bulk of supply lie? In the hands of a small group of individuals or across a significant number of holders?
- Who's behind the project? Are team members' identities known and do they have previous experience in this space?
- Do they have an active community? Are their social media channels active? Follower count isn't a good metric as they can be using bots.
This information can be gathered from the project’s website and published documentation. You can also join their social media channels (eg.: Discord) to probe for this information and gain a feel for the community.
NFT scams
NFTs (non-fungible tokens) are more than just collective digital assets. They are a form of artistic expression and an investment tool, revolutionising the art world and the creator economy.
They can be used as an investment asset, proof of ownership, access to a service or community, played in games, and sometimes all of these features combined. NFTs can come in a variety of different forms, such as art NFTs, music NFTs, video NFTs, game NFTs, etc. Unfortunately, due to its popularity, the NFT space also attracts bad actors.

How to avoid NFT rug pulls?
NFT scams, also known as “NFT rug pulls”, occur when the team of an NFT abandons the project and vanishes with users’ money (pulling the rug from beneath everyone's feet).
Common red flags are anonymous and unknown (anon*) team members, low liquidity and an unrealistic roadmap. Let’s take a look at each one.
*Some anon’s are well known and have a great reputation
- Team and community. Check the project’s social media channels and website. Are they active, or is it a bunch of bots? Does their website look professional or is it copying from other projects? Have team members worked on other projects before and are their identities known? Legitimate NFT projects have an experienced team and a proven track record.
- Project’s liquidity. NFT projects with low liquidity make it difficult for investors to convert their NFT into other assets. You measure liquidity by the NFT’s trading volume. A high trading volume means that there are people actively trading them. A low trading volume means a small number of people trading, which could point to a rug pull scam.
- The roadmap. Does the project roadmap include clear milestones? Do they have short, medium and long term goals? What are their plans for marketing and growth? Is the roadmap too good to be true? Then it probably is. Scammers get users excited with an ambitious roadmap and end up not following through with their promises. Consider NFT roadmaps with realistic goals.
Even if you take all the precautions above, there is still risk.
The community may be active, the team may be doxxed (their real identities are known), and they have a budget to keep building.
But issues happen. Team members may leave the project for whatever reason, they may face a regulatory or legal hurdle, their social media channels hacked, or another hurdle that impacts negatively on the project.
Learning to identify these red flags can help you save time and money from what could be a scam later down the line.
Phishing scams
Phishing is a type of social engineering attack where the scammer “fishes” for personal information, such as credit card details. They pose as a credible business or entity with the intent of deceiving their victims.
It’s “social engineering” because it’s not hacking a system, but rather the person.
You may have your assets securely stored in a vault somewhere on the blockchain or in a hardware wallet, but humans are fallible and subject to manipulation.
How does phishing work?
The typical phishing attack is done via email. The victim receives an email from someone they trust, alluring them to click a link, download malware or give away their personal information.
Attackers usually go for their victims’ bank accounts and credit card information. With Web3, it may be your wallet details or exchange login.
Here is an example of a typical phishing email. The crypto exchange Binance also has several good examples of phishing emails in their help centre.
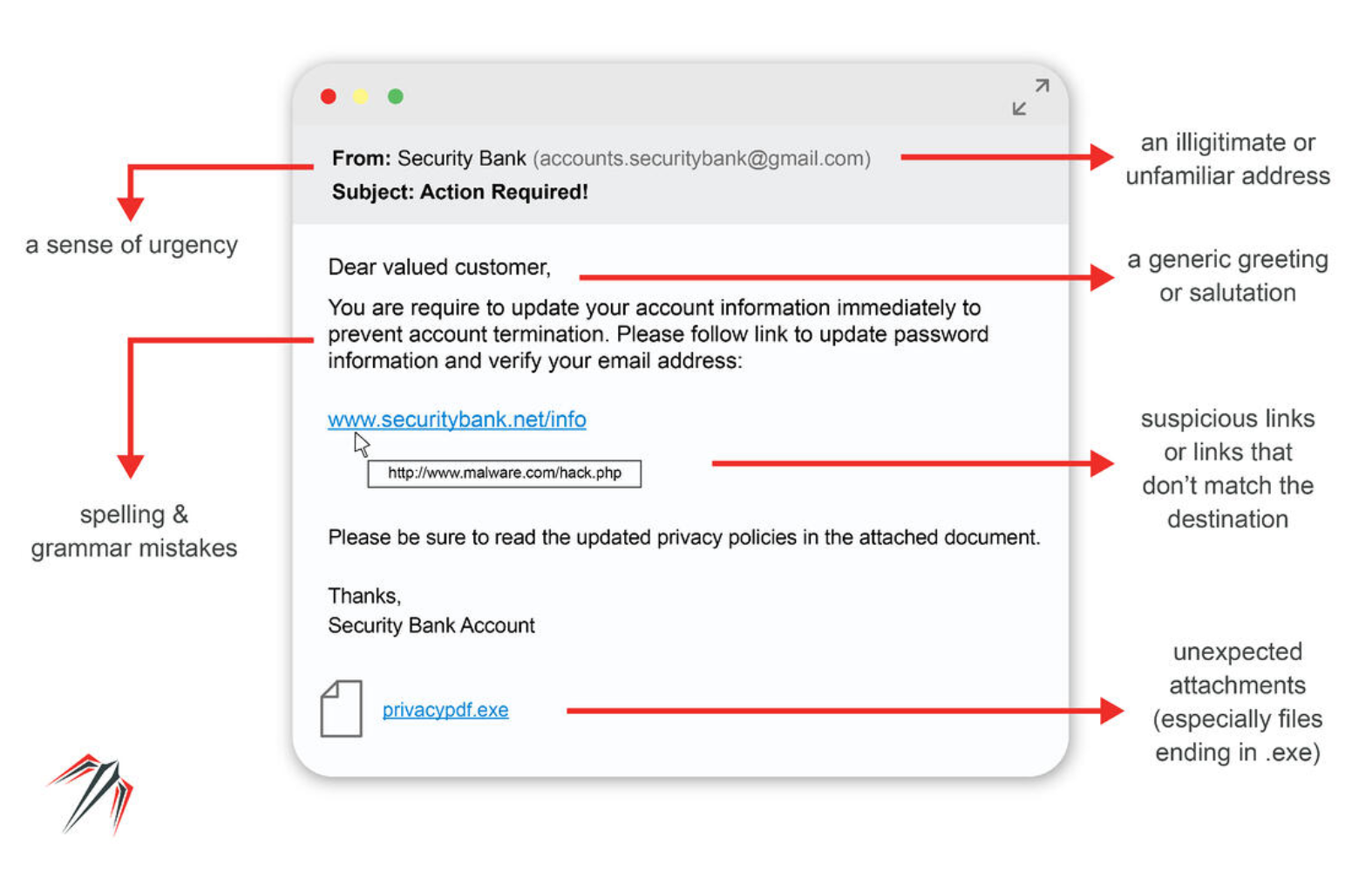
How to avoid phishing?
Some exchanges have an “anti-phishing” code. It’s a unique set of characters that appear in legitimate emails sent by these companies, usually in the header or footer. If the email lacks that code or is incorrect, it’s a phishing scam and should be reported to the company.
Bookmark your frequently visited websites. Don’t trust links on search engines. Scammers may post ads on Google to have their link on top of the page. The user clicks the link and lands on a replica of the exchange’s website. They login with their username and password, unknowingly giving these details to the attacker.
Stay calm and be diligent. Be wary of links in emails and unknown websites. Check if the sender’s email address matches the real entity sending it. Check if it’s the legitimate domain address (eg. FTX.com and not FTX.xyz). When on the website, double check that you are in the correct URL (eg. https://ftx.com) of the company, and not a replica.
The Federal Trade Commission of the United States government published information on phishing scams and how to avoid them. It’s a short and quick read.
Peer-to-peer scams
Peer-to-peer trading (P2P) is a method used to allow people to buy, sell and trade cryptocurrency (and just about anything) without an intermediary. Individuals can trade directly among themselves in real life, or via online platforms where they meet as buyers and sellers.
The P2P space has known its share of scams and thefts. Things have improved with new escrow methods, trusted facilitators (online platforms) and via KYC (know-your-customer) validation.
But there is still risk.
Here’s how to avoid some common scams on P2P platforms so you can trade safely and securely with other people.

Fake receipt
It’s not that difficult to manipulate photos and screenshots. The attacker sends its victim an image, claiming they have done their part of the trade. They may add a sense of urgency, to pressure the person in following through their end of the deal.
The victim forgets to check if they’ve received the money they were meant to receive, sending the attacker the goods and receiving nothing in return. Don’t allow yourself to be rushed, and verify if the other party has done their part of the deal.
Chargeback
Some P2P platforms have a chargeback feature. Chargeback is when the money is returned to the buyer (the one paying), which in this case is the scammer. The scammer triggers the chargeback, requesting for the payment to be undone.
Similar to the fake receipt, the seller may be given a sense of urgency to approve the transaction without checking if the money was sent to their account, being left with no money nor the agreed asset. Don’t trust, verify if the other party has done their part of the deal.
Unknown transfer
Sometimes scammers just let the P2P transaction proceed as normal. Once it’s done, the scammer contacts the bank to cancel the transaction, claiming something wrong with it or that they were hacked.
The victim then loses their money because they already released the crypto. They may even be bullied or blackmailed to not report the scam to their bank or the police. Don’t let yourself be intimated. Report to the authorities and to your bank what happened.
Cheques
A cheque scam is when the scammer chooses a supported payment method initially, but then pushes the victim for using a cheque. Their intention is to scam the counterparty out of their crypto, while appearing to be following through with their part.
The most common scenarios are cancelling cheques after invoicing them and bouncing cheques. To be on the safe side, never accept payments via cheque.
Romance scams
The FBI warned of a rise in online dating scams in 2016. These are not completely new or even dependent on crypto, as they existed since the 90s from the days of IRC. However, with crypto, bad actors have additional forms of receiving payments from their victims.
While anyone can fall victim to these scams, older people usually suffer heavier losses. Scammers target them because older people may be more susceptible to manipulation and because they have free capital available (pensions, homes).

Most common romance scams
Inheritance scams. A scammer poses as a young woman, claiming they are to inherit a large amount of money or gold from a male relative. They need to marry in order to receive the inheritance, an apparent prerequisite in their country of origin. Unfortunately, they cannot pay for the duty or marriage taxes.
They ask the victim to send them money for the flight and to bring them the gold. They state they’re flying over as a gesture of good faith. The victim sends the money and the “young woman” never arrives, nor does the gold.
Intimate scams. The victim is contacted by a potential suitor on social media. During their courtship period, they arrange to meet online, but the webcam is apparently not working on that day.
Through flattery and persistence, they convince the victim to undress or perform other intimate acts. They then reveal the scheme and threaten to share the video on social media for everyone to see. The victim may comply, but new demands continue to arrive.
Verification scams. Common on social media sites, the victim is contacted via email or text asking them to verify their account. The message disguises as an official communication.
The app requires users to verify due to a policy change or update to their services. The victim is encouraged to click on a third-party link to verify their account, giving away their personal information, such as name, email, social security number, and sometimes bank account or credit card details.
Fake dating scams. Some free online dating sites may appear legitimate but are later found to be honeypot scams. Their goal is to harvest information from users. Some go a step further by offering a premium membership in exchange for completing a survey, where the victim fills additional details, such as their bank account.
Users should also be wary of a sudden influx of attention after creating a profile. If a user profile has limited information and is receiving messages from potential suitors, is most likely a scam attempt.
Military scams. Posing as a fake or sometimes actual soldier, scammers connect with their victims and try to create a bond with them . The “soldier” has undertaken service for their country, may be near the end of their careers, with children, widowed, and other sad circumstances.
After building a relationship they send requests for money, perhaps to pay for a flight home, or medication for an injury sustained while in service not covered by the government. The requests can drag on for months. The US Army even has an educational article to help people spot these scams.
How to avoid romance scams
Here are quick tips on how to avoid romance scams. This is not an exhaustive list but will keep you safe from this type of scams. Please report scammers to the social media and other platforms where you’re interacting with them.
- On social media, don’t accept friend requests from users you don’t know.
- Use reputable dating sites and keep the communication in their app.
- Don’t reveal personal information with users you’ve been chatting online with.
- You can be blackmailed. Don’t send compromising photos/videos to others.
- Be wary of links, don’t click and don’t download suspicious apps.
- Never send money, gift cards or bank account information to others.
Conclusion
Scammers want easy pickings, so they go after people using methods they think will have better odds of defrauding their victims.
There is a common misconception to think that only older people, those with intellectual disabilities or disenfranchised are the type of people that fall for scams. That’s not true.
Smart and bright people are defrauded every year. Blockchain developers and engineers have been scammed into giving away their NFTs, tokens or access to sensitive information.
With this post, we hope readers leave better informed and equipped to handle the most common scams that happen inside and outside of crypto.
Further reading
How not to be scammed in NFTs | by Maï Akiyoshï | Medium
5 Common Cryptocurrency Scams and How to Avoid Them | Binance Academy
Romance Scams & Online Dating Scams (kaspersky.com)
Crypto Security 101 (rabbithole.gg)
